DreamHost, a web-host, has revealed that they are fighting the US government warrant requesting all information about every person who has visited the website www.disruptj20.org. Such information could include all subpages of disruptj20 that you surfed, how often you did so and the complete text of anything you might have typed into the page (such as donation or sign-up information).
How many web-hosts and Internet service providers fulfill such requests without a fight and without letting its users know?
That’s why we recommend anonymizing your web browsing with the Tor Browser.
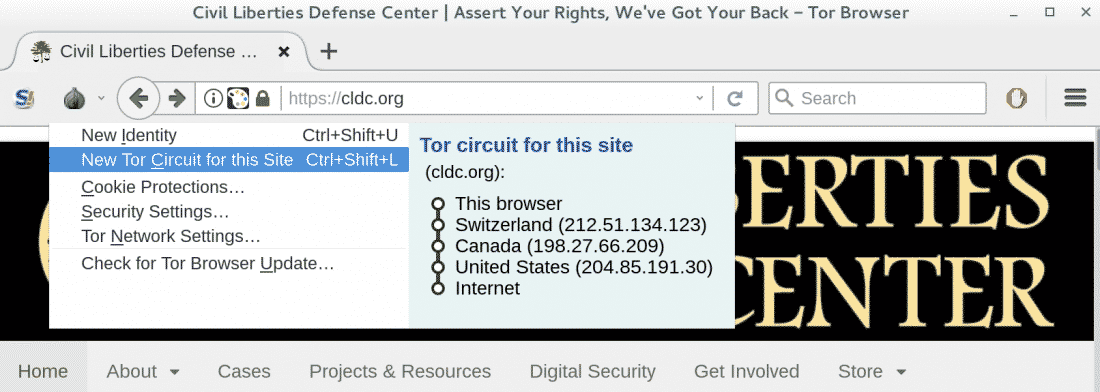
Proper use of the Tor Browser would protect your identity from such overreaching requests. Tor works by routing your traffic through a sequence of servers (shown in the Tor circuit above) using layers of encryption (like the layers of an onion — Tor stands for The Onion Router). These layers of encryption guarantee that a server in the sequence only knows about the hop before and after itself. In the example above, all “Switzerland” knows is that you are accessing the Internet via Tor (i.e., not what webpage you are requesting) and all the “United States” knows is that someone is requesting the CLDC website via Tor (i.e., not who you are or what your location is).
We recommend using the Tor Browser for browsing any webpage on which you don’t need to enter any personally identifiable information. (If you log in to a website, the webhost would know your username, possibly identifying you.) It’s easy! Just download the browser and use it as you would Firefox or Chrome. If you are finding that your web browsing experience is hampered, try one of the following:
- Click on “New Tor Circuit for this Site” (via the onion icon in the picture above). Downloading speeds are only as fast as the slowest server in your circuit, and some servers are slow — requesting a new circuit of servers might fix this. Also, some websites block Tor by blocking particular servers that make up the circuit. If you can’t reach a website, requesting a new circuit might help.
- Try adjusting the “Security Settings” (also from the onion icon to the left of the web address bar). Lower security often improves performance playing videos and some other website features (with a small increased risk to your anonymity).
Another tool many use for anonymous browsing is the Virtual Private Network (VPN). A VPN works as a middleman. You send all your web requests to a VPN provider of your choice (via an encrypted channel) and the VPN provider fetches the pages from the Internet for you. All a webhost would see is that a VPN provider is requesting and sending information (and nothing about you, unless you have entered personally identifiable information into the page). Of course, that VPN provider would be able to record your detailed browsing history, so you are putting a lot of trust in them for that reason. VPN providers can be one-stop-shops for government requests of information, so if you use a VPN, choose wisely.
As a final note, Tor is not perfect (no security tool is). One way that Tor users can be de-anonymized is via a timing or correlation attack where the attacker first observes (1) traffic accessing the Internet via Tor and (2) traffic being requested from the Internet via Tor and then tries to match up (1) and (2). However, this requires access to monitoring web traffic on a global scale and is likely only possible by nation-state adversaries. A common mistake is logging in to a non-anonymous social media or email account in the same web browsing session–this can easily let your Internet provider, social media/email platform and other webpages (via “Like” or similar buttons) know your true identity and what you’re trying to browse anonymously. It’s best never to log in to social media or online accounts from Tor, unless you have a good reason. Finally, when using Tor, keep in mind it only provides anonymity — for privacy, you need to be accessing webpages using end-to-end encryption via HTTPS (though unfortunately not all websites support this).
To learn how to make the most of anonymous web browsing and other in-depth digital security trainings, please contact us.
Published August 16, 2017
