Vulnerabilities and exploits to Internet-enabled devices are constantly being discovered (and stockpiled). This is one reason why you’ll hear us say “there is no such thing as perfect digital security” and “don’t bet your life and liberty on this [digital security] tool”. That said, there is a lot you can do to protect yourself and your communities! Our recommendations (check out our Introduction to Digital Security for Activists) will keep you safer in many situations, even if there is a hidden, fatal flaw in any single layer of protection.
A few days ago, university researchers announced a vulnerability in almost all WiFi networks’ security. This is a great time to go over the risks and best practices in connecting to the Internet via WiFi. A secured WiFi network is one that you need to enter a password to join the network—it encrypts information being exchanged between you and the WiFi access point. If no password is needed to join, you’re connecting to an open network—note that many hotels, corporate coffee shops, trains, buses and airports allow you to join their WiFi network without a password, but then you get directed to a login webpage, usually with branding and advertisements, where you need to enter in a code or room number or something in order to access the web. Such a network is not secured but simply limits access to “valid” customers. This recently-announced KRACK vulnerability that is causing so much anxiety essentially just turns a secured WiFi network into an open WiFi network.
So the best way to protect ourselves from a range of threats is to get in the habit of always using additional layers of protection—layers of encryption—when we need to access an open or “secured” WiFi network. Here are some layers of protective encryption that you can use (for example, when browsing the web):
- VPN. A VPN is a middle man that routes all your traffic through a remote server, thus hiding your actual IP. The VPN provider knows all your web-browsing behavior, but encrypts traffic between you and the VPN server. (Never use a VPN if they do not give provide an encrypted connection to their servers.) Read our post on anonymous web browsing for more info.
- Tor Browser. The Tor Browser adds layers of encryption between you and the server of the webpage you are accessing. Its main purpose is providing anonymity (which we discuss here), but also adds a layer of encryption between you and the last node on your path through the Tor network.
- HTTPS. Whenever possible, access pages using https, even if you are using a VPN or Tor. If you do not see the lock icon or the URL doesn’t start with https:, then it isn’t using https; https encrypts the traffic between you and the server where the webpage is stored. The browser plugin HTTPS Everywhere will ensure you are accessing a webpage using https, but only if it is available. Some websites don’t support https and other https pages will have some content (like images and ads) that is delivered without encryption. (In some browsers, this will cause the lock icon to disappear.) While you can configure HTTPS Everywhere to deny all non-https traffic, you might find your web browsing too restricted. This is where other layers of protection come in. Just remember, HTTPS is the best! It’s the only thing that can protect information you submit (including passwords) from evil—as in untrustworthy, malicious, or compromised—WiFi networks or administrators, evil VPNs, or evil last-Tor-nodes.
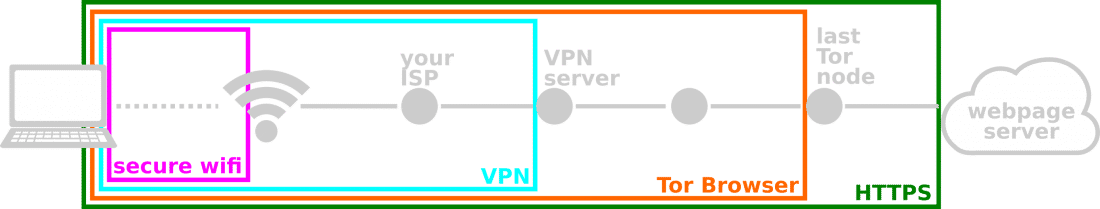
To snoop on your data, consider where on the path between you and the webpage server your adversary is. A State-level adversary would have access to your data almost anywhere on this path, but even a State-level adversary would have difficulty knowing that you are connecting to the particular “last Tor node” (because of how Tor works). A local snoop would need to be physically near you, but would need to break through many layers of encryption. (Note that because of how much information your VPN service provider knows about your browsing behavior and because Tor may not allow you to access all web resources, we recommend you use a VPN sparingly and understand that risk.) Using more than one layer of protection will protect you if one layer fails … there is always a chance that all layers will fail, but those chances get smaller and smaller the more layers you use. (We think 2-3 layers—secure WiFi plus HTTPS plus the Tor Browser—is a great choice.)
Since you can’t necessarily use all the layers of protection at all time, be wise about how you are connecting to the Internet and use protection.
