End-to-End Encryption is the best security model for communications or online document storage, but the term is a bit of a mouthful that isn’t always clear (“the ends are me and the server, right?” — wrong!). So let’s try using a new term — Direct Encryption — meaning: the only people who can decrypt and read messages are those directly involved in a private conversation or project. Crucially, these are also the only people who control the encryption keys. Direct Encryption powers many of our recommendations: PGP/GPG (Thunderbird+Enigmail), Wire, Signal, and Cryptpad.
(We chose this term in part because of philosophical parallels to Direct Action, wherein groups often work to achieve their goals in the belief that powerful entities, like the State or large corporations, cannot be trusted. Also, good security culture practice means information is handled on a need-to-know basis.)
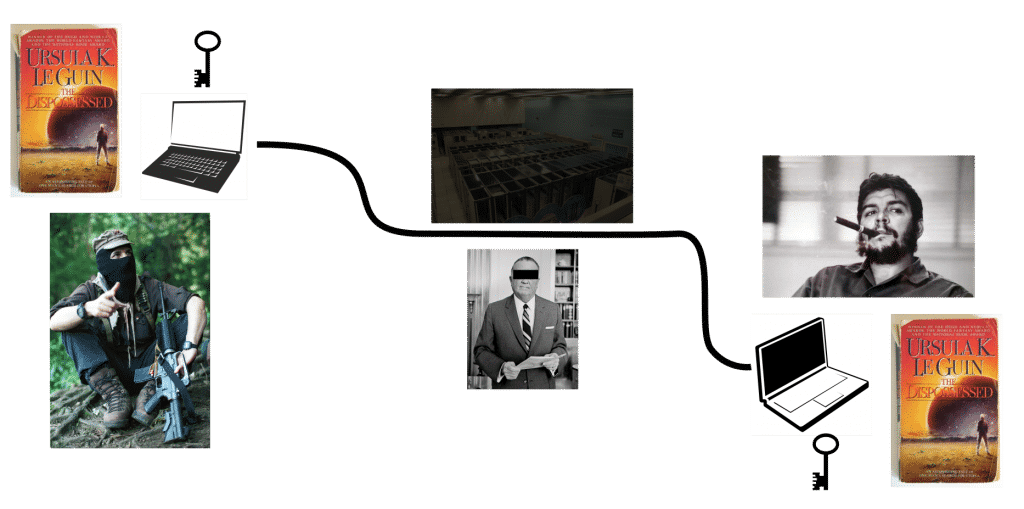
Here are some pictures to illustrate why Direct Encryption is so important in private messaging. Marcos (left) is trying to get a message (Ursula K. Le Guin’s the Dispossessed) to Ernesto (right) using laptops and the Internet: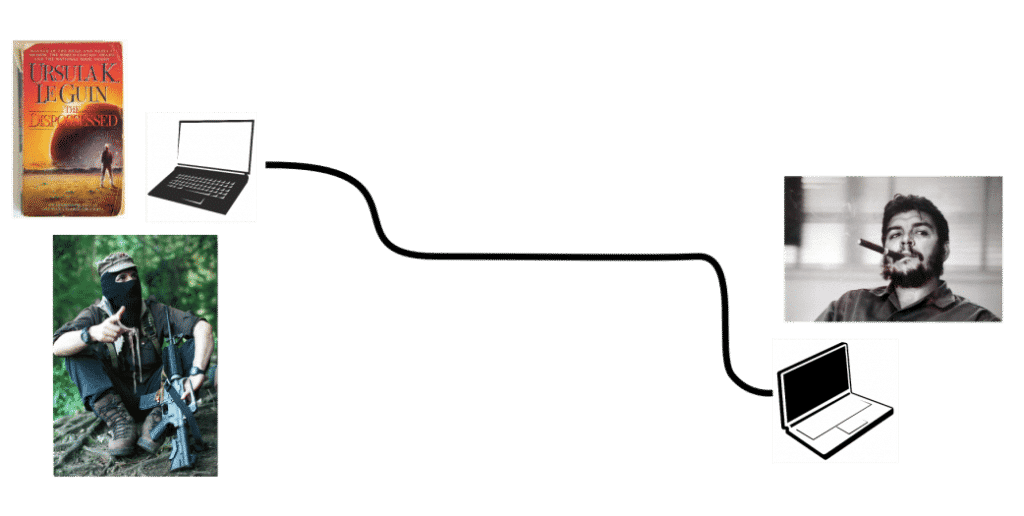
But the ghost of mean old J. Edgar Hoover haunts the infrastructure. The Man in the middle here is able to intercept, read, and change any unprotected message sent between our two heroes. Like so:
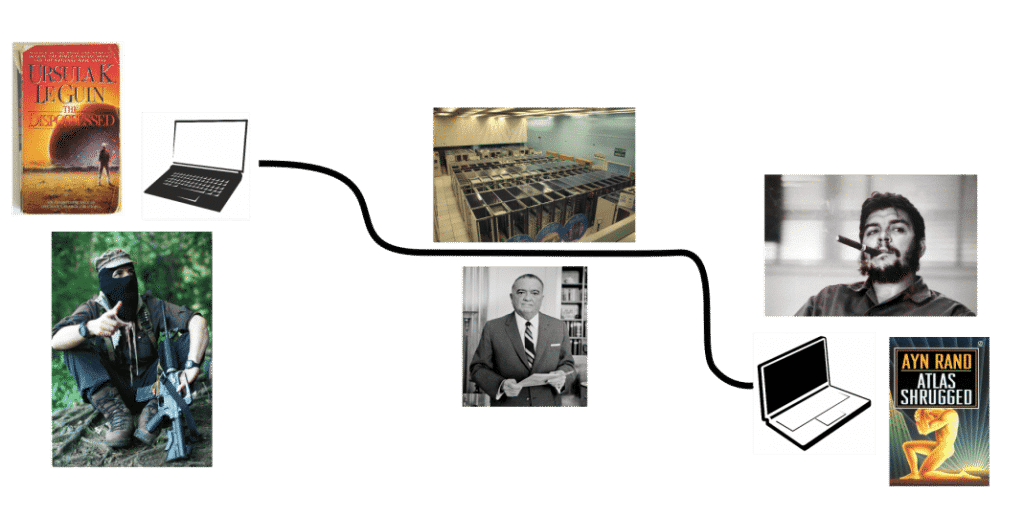
(Edgar could also just read and send the message along unaltered). To make matters worse, saying that an app uses “encryption” (without being specific about who holds the keys) doesn’t guarantee that messages remain private and authentic. For example, if a server between the two comrades is managing the encryption keys, anyone with access to the server could read and modify all messages between them:
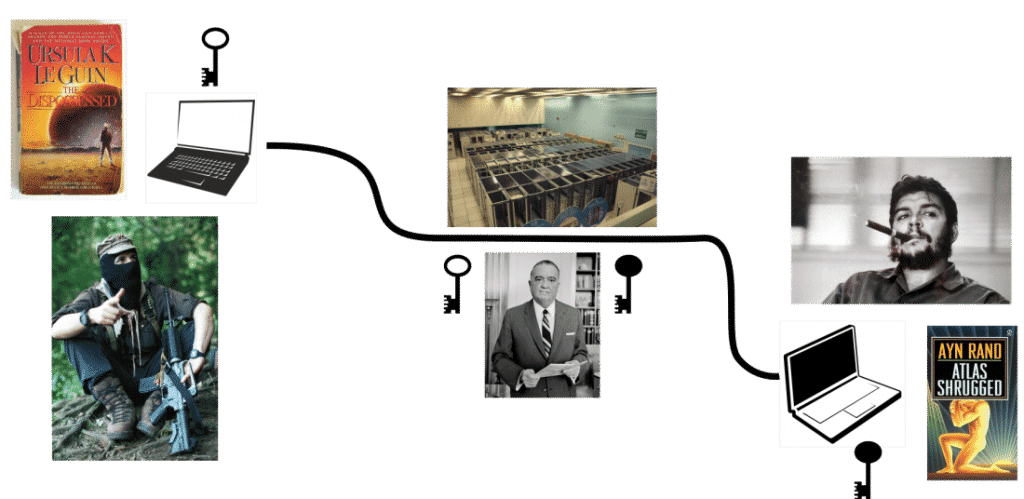
If Direct Encryption (end to end encryption where only the comrades hold the keys) is used, there is no way for an adversary to see or alter the message. Hooray! Like so:
How do you know whether an app is using Direct Encryption? There will be some way to manually verify encryption keys — Signal makes this super easy with safety numbers and Wire uses traditional fingerprints that will be familiar to anyone who’s used GPG. Wire uses a unique key for each of your devices, so verifying fingerprints can get cumbersome if your friends each use multiple devices. The advantage, though, is that with Wire or GPG it’s easy to post your fingerprints in multiple public places — like social media or your organization’s website — and ask friends to copy/paste/find to verify them. Also, if a device is lost or stolen you can remotely invalidate its key so the compromised device can no longer be used to read or send encrypted messages.
Remember, it’s crucial that any Direct Encryption app is open source, so that its security features can be verified, and its security and usability can be publicly criticized then improved.
Another way to reduce exposure to a malicious interloper is through peer-to-peer messaging, where it is commonly said that there is “no server” used to relay your messages. This approach can certainly help, especially if it means moving away from Google or Facebook as your chat server. On the other hand, the argument about removing “the server” from your conversations can be misleading: there is a ton of Internet infrastructure in between you and your friends, it’s just invisible to most users and apps. But this infrastructure is precisely what the State exploits to conduct suspicionless, mass surveillance.
Stay safe out there!